Understanding Public Key Cryptography
When using encryption, it is helpful to understand some basic concepts. Don't worry, we won't get into the math, we are going to keep it really basic. But since encryption, like other digital technologies, is such an important part of modern life, this is really something that everyone should have some basic understanding of. I mean, this is the stuff that keeps your bank account and financial transactions safe online (I won't get into much of that because I'm focusing on encrypting email). You can skip this section if you want, but I highly recommend reading it.When encrypting something you use some password, or key, to encode the information in such a way that it can't be deciphered or read without a key. It used to be that in order to use encryption, you had to arrange in advance for both parties to have the same key. It had to be exchanged in secret, because anyone who knew the key could also read the messages that where later encrypted with it. With this method, you need a separate key for each pair of people who want to communicate securely and they all have to be exchanged in secret! So this can quickly become unwieldy. This method is called symmetrical encryption, because the process works the same both ways. The same key that was used to encrypt the data can also be used to decrypt it.
Public key cryptography, however, is asymmetrical. The key that is used to encrypt a message cannot be used to decrypt it. Instead, there are two keys that are related: the two keys do the opposite of each other. So the keys come in pairs and something that has been encrypted with one key must be decrypted with the other key, and vice versa. Since the key used to encrypt the message can't be used to decrypt or read it, it can safely be shared in public. This is why it is called public key cryptography. Of course, this means that the other key of the pair must be kept secret, hence it is called the secret or private key. So, once you have created such a key pair, you put one away to be your secret key, and the other you can publish to all of your friends. Anyone can then use the public key to encrypt a message to you. Since the key you kept secret is the only way to reverse the process and decrypt the message, you will be the only one who can read these messages.
The only thing your friends need to do then is to verify that the key they are using actually belongs to you. Of course, if they use a key that really came from someone else claiming to be you, then that person can read the messages they intended to be secret. You can meet in person to verify that they have the right key, but it doesn't have to be in secret. The software will give you a fingerprint, a short sequence of characters, that identifies the key. You can compare the fingerprint of your key with the fingerprint of the key your friend has received, if the fingerprints are the same, so are the keys they came from.
Digital Signatures
Public key cryptography also gives us a way to verify who sent a message. Remember that anyone who has your public key (which really could be anyone), can encrypt a message to you. So how do you know who really wrote the message?Let us suppose that you and a friend each have your own key pair, and that each of you has the other's public (but not private) keys. In order for your friend to send you a message, he encrypts it with your public key, so that only your private key can decrypt it. Now, what if he encrypts it instead with his secret key? Remember that the keys do opposite things, so if it was encrypted with his private key, it can be decrypted with his public key. At first this might seem useless. Since everyone has access to the public key, anyone can read the message. But once you do, you know something about it that you would not have known otherwise. That message could only have been written by someone who had access the secret key that goes with the public one you used to decrypt it. If you have verified that the public key belongs to your friend, and he has properly kept his secret key secret, you know the message is from him. This is called a digital signature.
Of course, you can use both processes on the same message, this way when your friend reads it he knows both that it came from you and that no one else could have read it. Or you can sign a message without encrypting it, so that anyone can read it, but they can verify who wrote it if they have ever verified your public key.
So, how do we go about creating a key pair and using it to encrypt (and sign) our email?
Installation and Configuration
While there are quite a few different applications that will allow you to encrypt your email, I'm going to explain how to use one particular set of software here. It is very likely that you are used to checking your email by logging into a website, but that doesn't work very well if you want to encrypt your email. Instead, we will be using Thunderbird, the email application from Mozilla, the makers of Firefox. It runs on Windows and Linux. (It also runs on Mac. I'm not giving specific directions for Mac here, but you can use a similar approach on a Mac.) Thunderbird doesn't come with the encryption features we want built in, but it has plugins just like Firefox does and we will use a plugin called Enigmail to add the encryption features we want. Enigmail doesn't do the encryption itself, it uses GnuPG, so you will need that as well. If you are running Linux, you probably already have GnuPG, on Windows you will need to install it as well.
Linux
If you are running Linux, you probably already have GnuPG installed and if you don't it should be available through your package management system. On Debian, you can install icedove (which is the Debian version of Thunderbird with a different name and logo). Ubuntu has a thunderbird pacakge. Or you can install the official Mozilla build. You may also be able to install Enigmail from your package management system to be available for all users, if you installed your distributions official package for Thunderbird or Icedove; however, I'm going to show later how to install the plugin from within Thunderbird for each user.Windows
First we need to make sure that GnuPG is available. There is a handy Windows package called GPG4Win, there are several packages available but for what we are doing you only need to install the Vanilla version. If you install the full package it comes with a different mail client, Claws Mail, which takes the place of Thunderbird. Feel free to try it if you like, but my instructions will be covering Thunderbird. Run the installer and just click through the "Next", "Install", and "Finish" buttons.Next, we need to download and install Thunderbird. This one is even a bit easier; it's just "Next", "Next", "Install", "Finish" and you're done.
Email Configuration
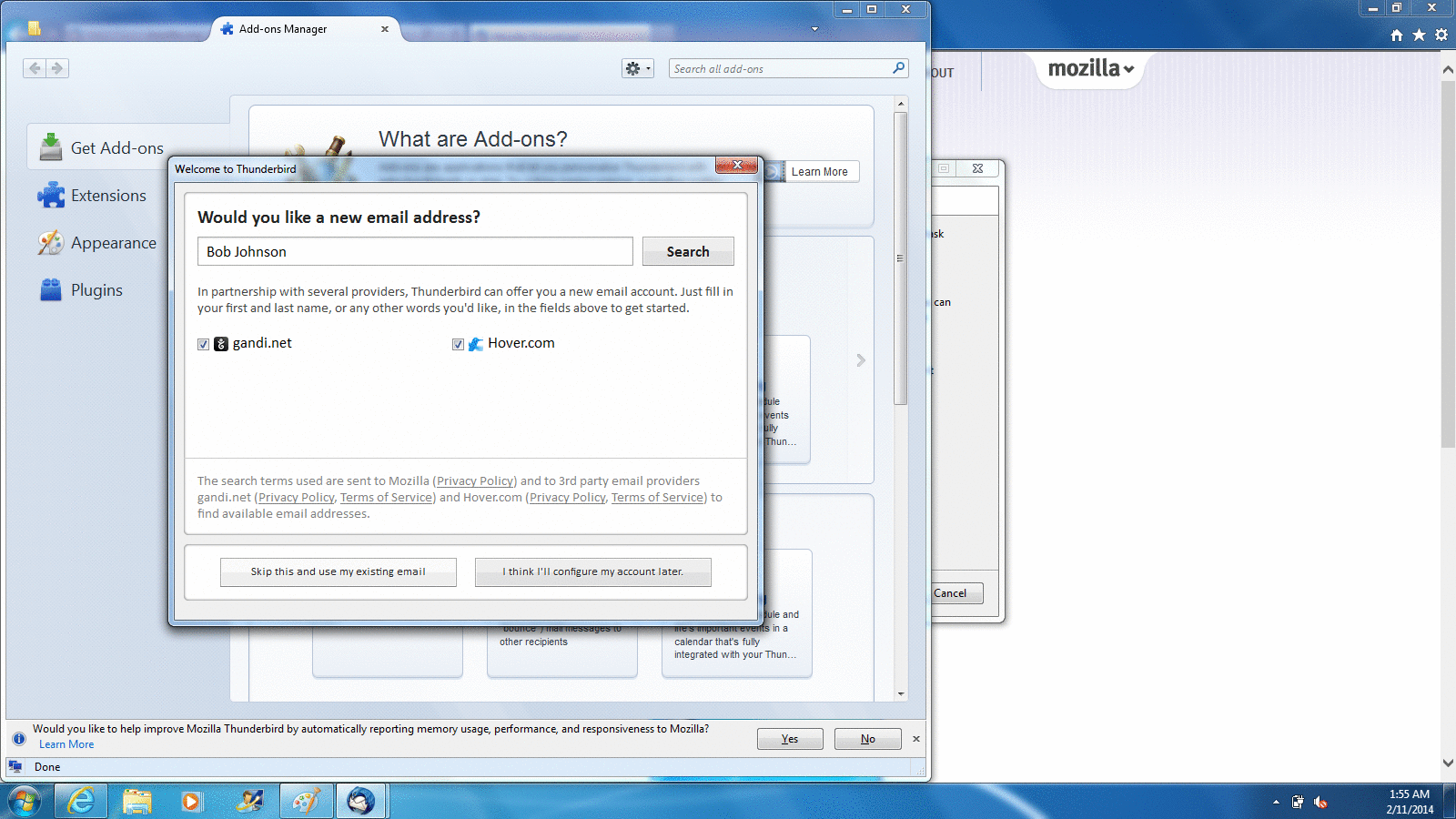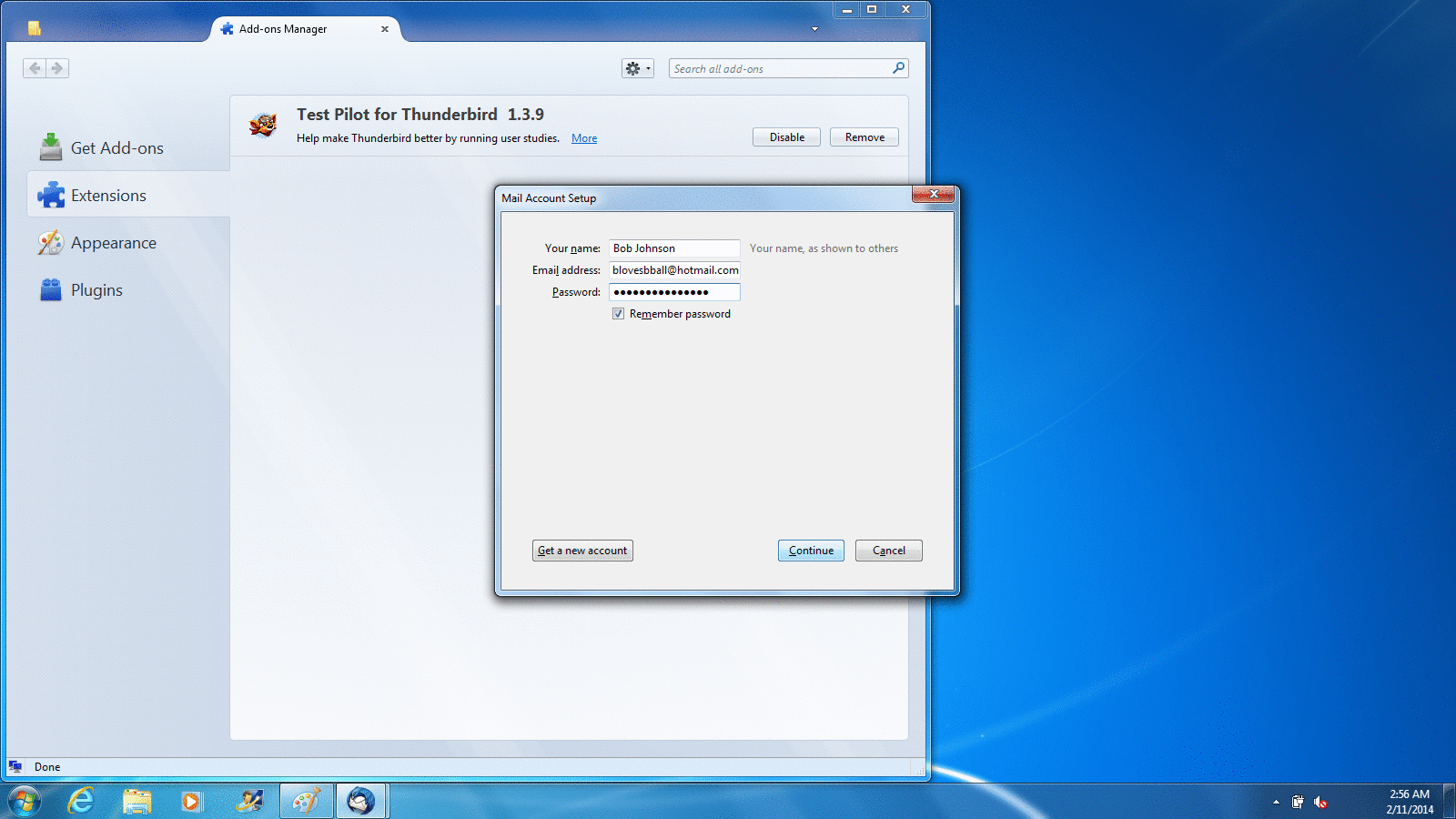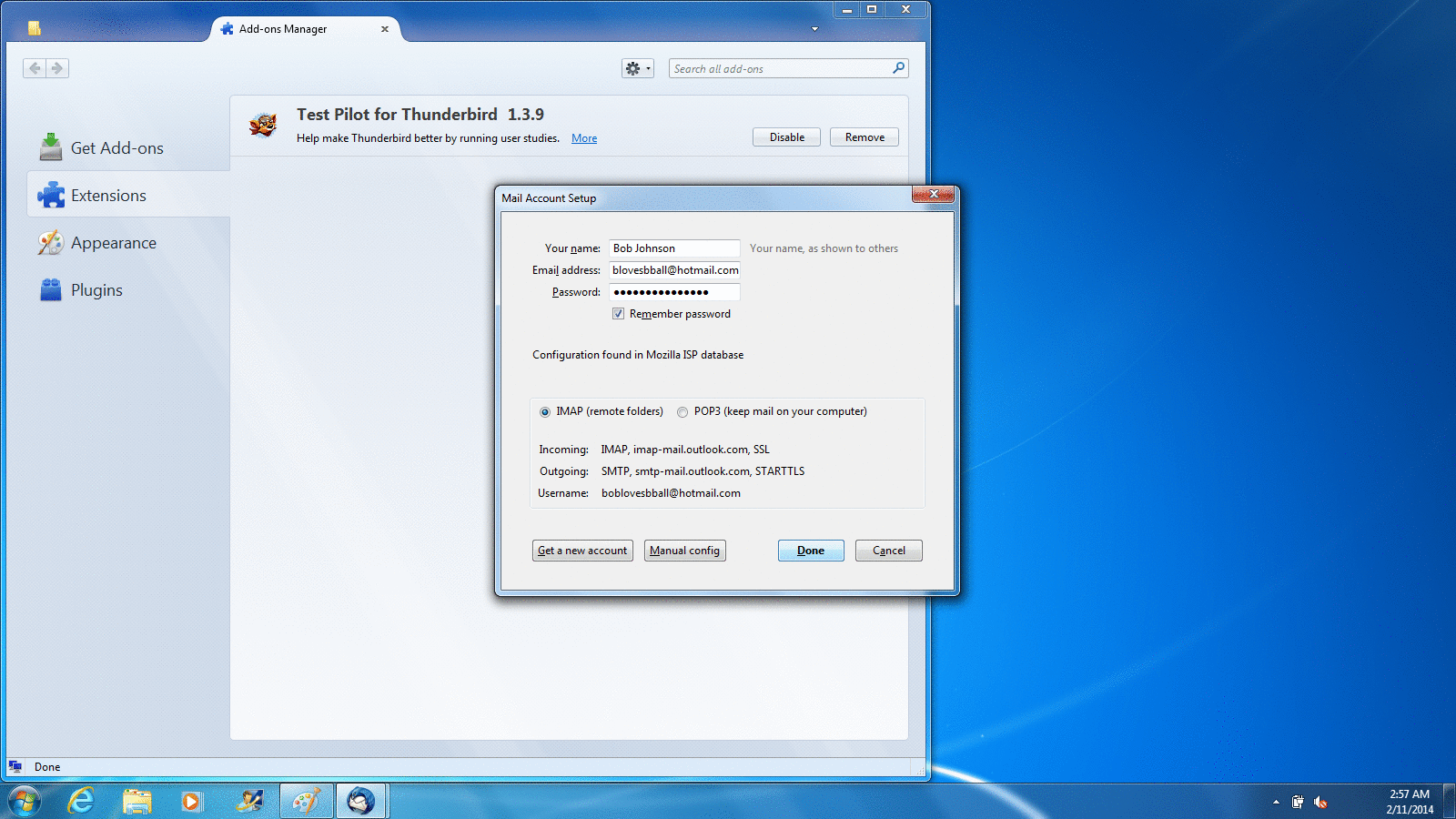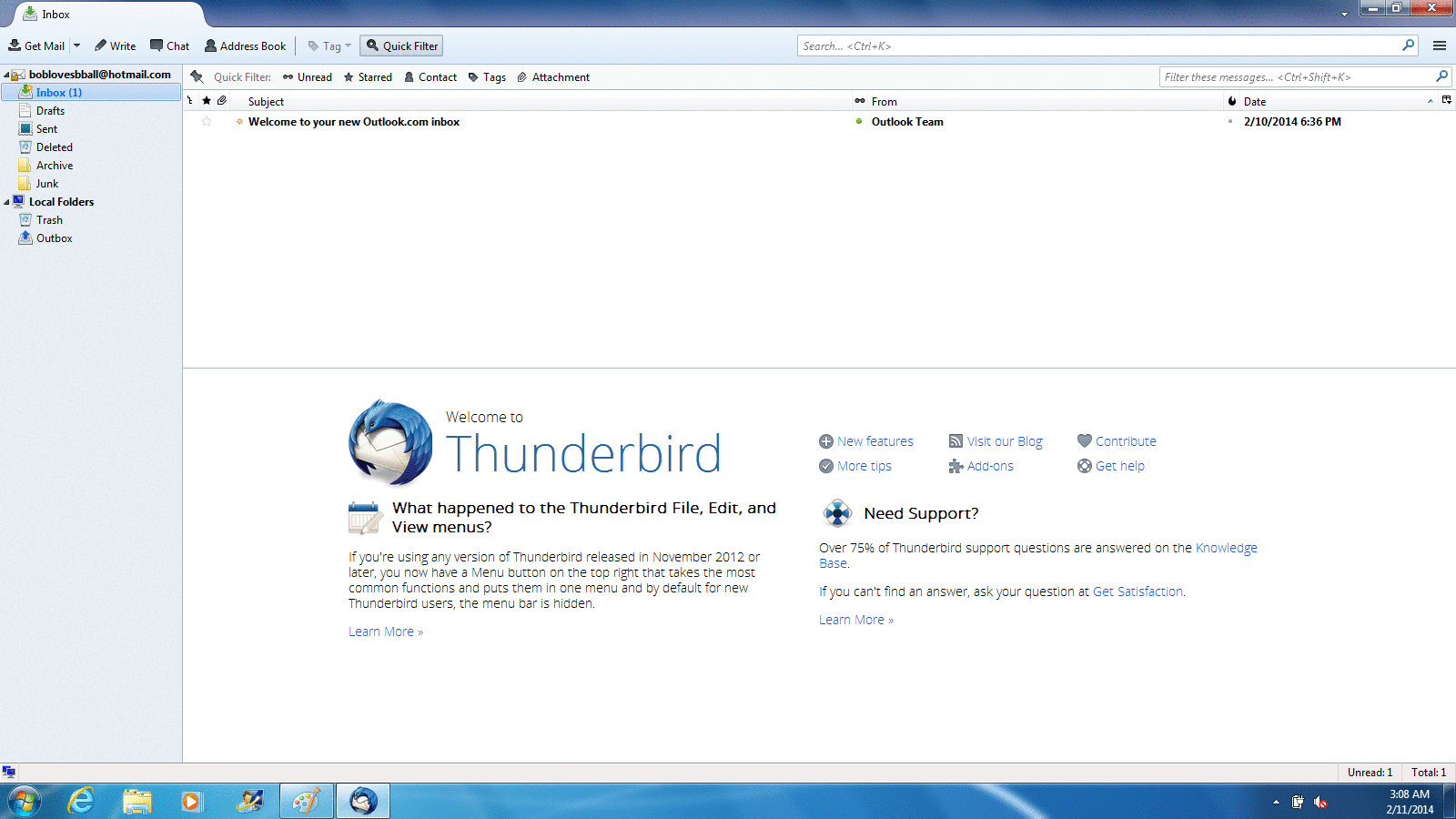
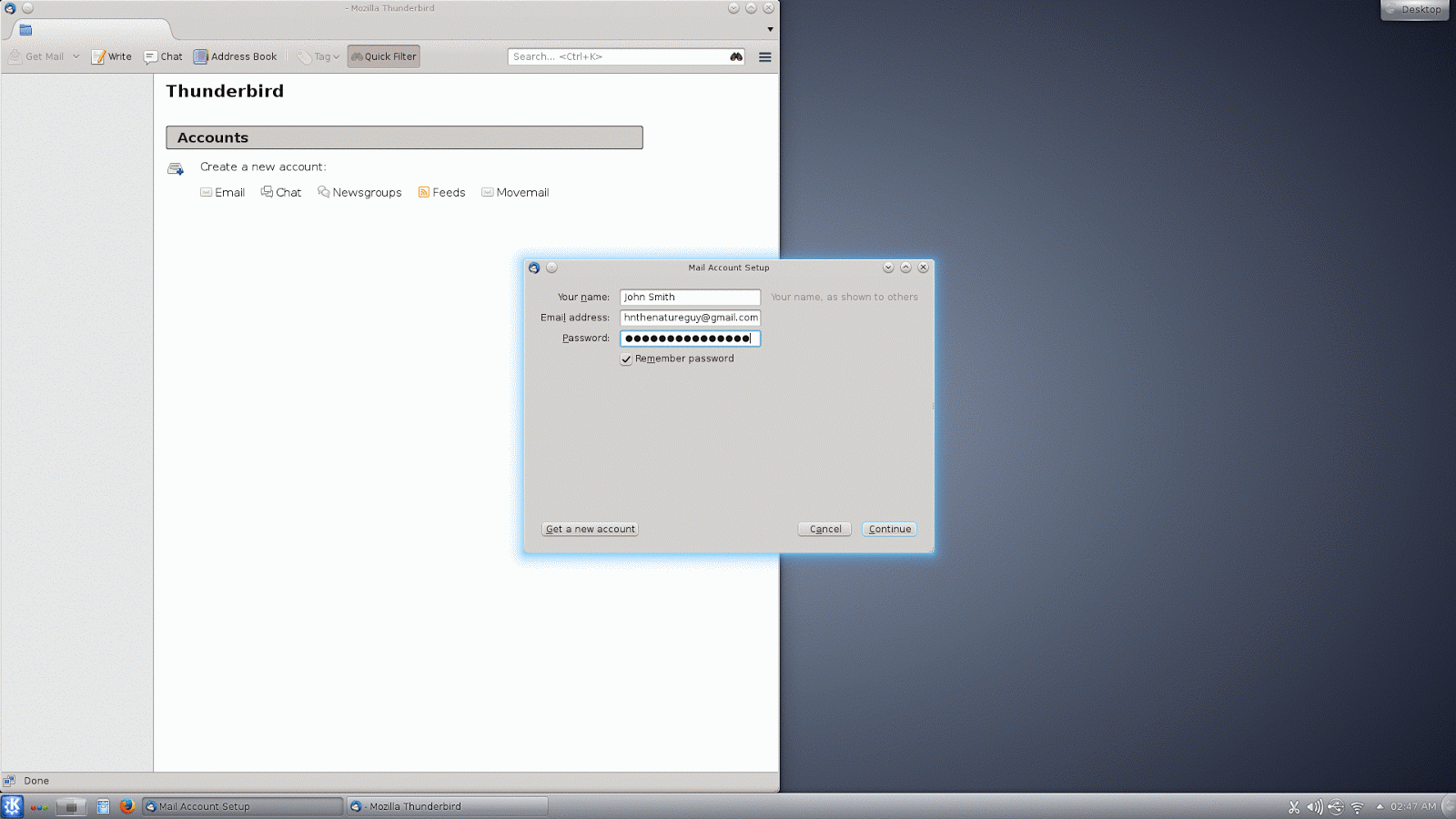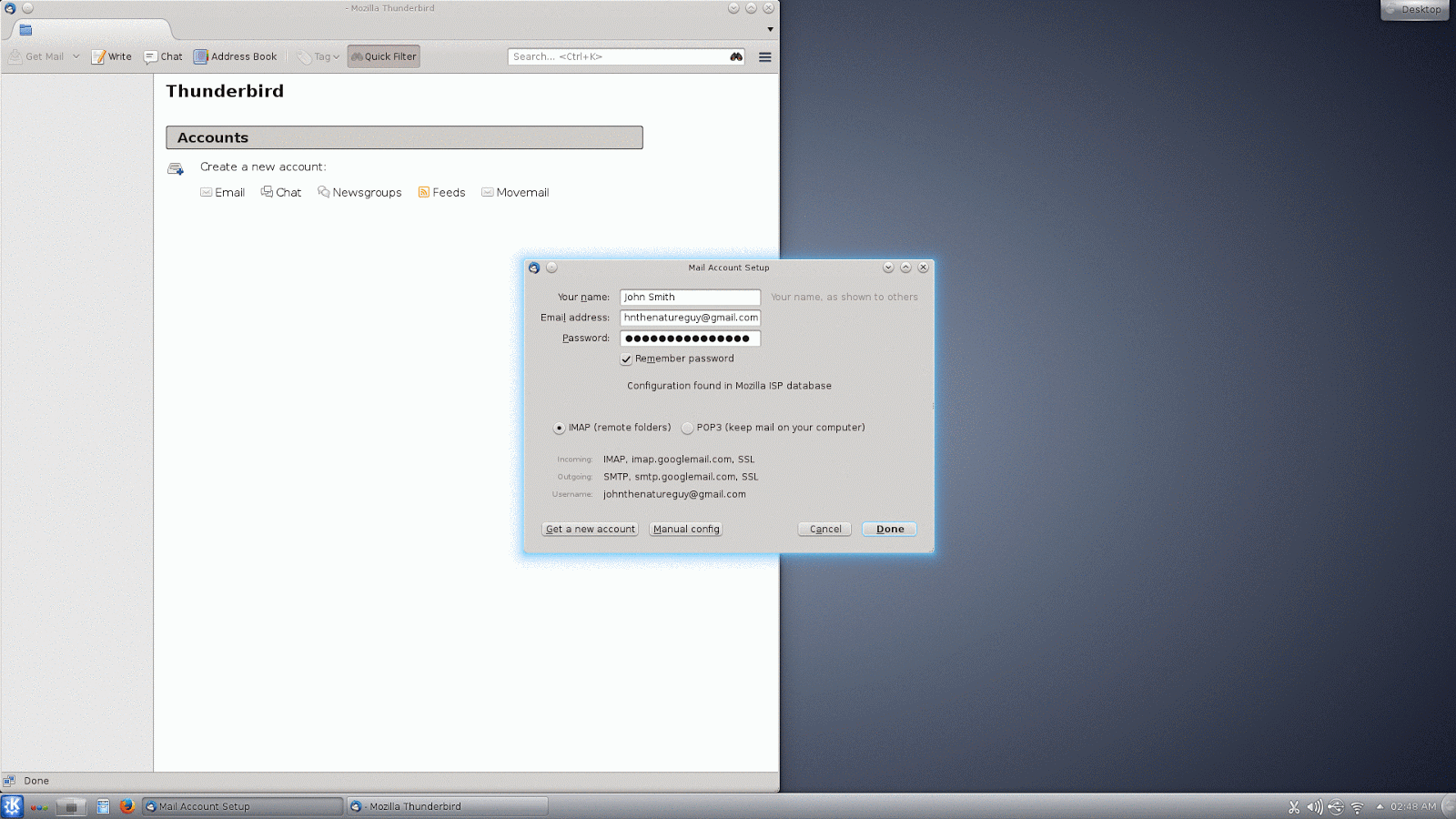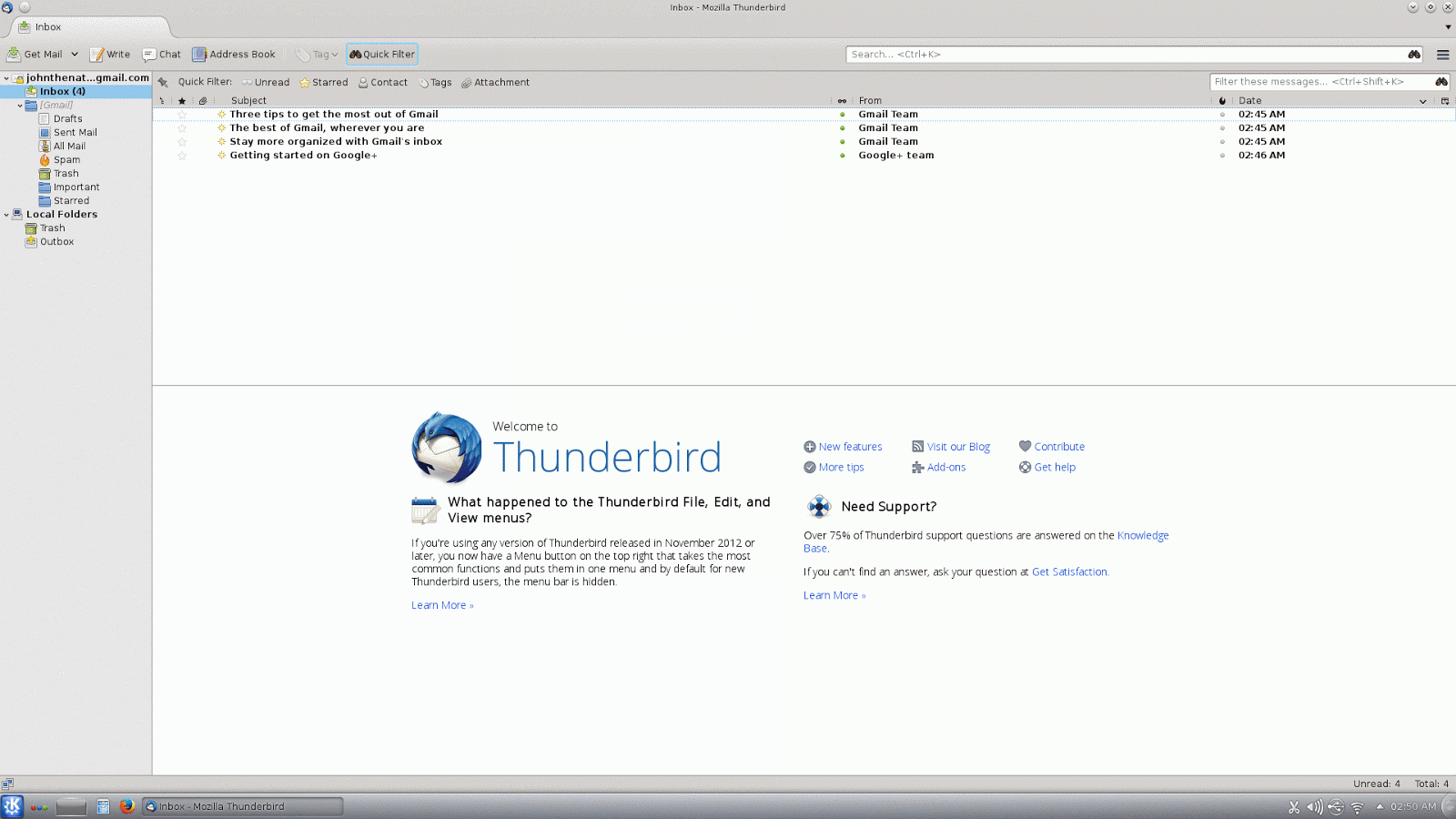
When you first run Thunderbird, it offers to set up a new email account for you. You can use this feature if you need a new address, but most people reading this will already have one. Thunderbird does a really good job of getting the correct settings for most major email providers, so usually all you need to provide is your name, email address, and password. If you have difficulty, you can contact your email provider to get the right settings to put in manually, or you can set up a new account to use with Thunderbird and Enigmail. In my examples, I'm using two of the more popular webmail services, Gmail and Hotmail, and Thunderbird determined the correct settings automatically.
Setting up a Hotmail account on Windows
Setting up a Gmail account on Linux (KDE on Debian)
Installing Enigmail in Thunderbird
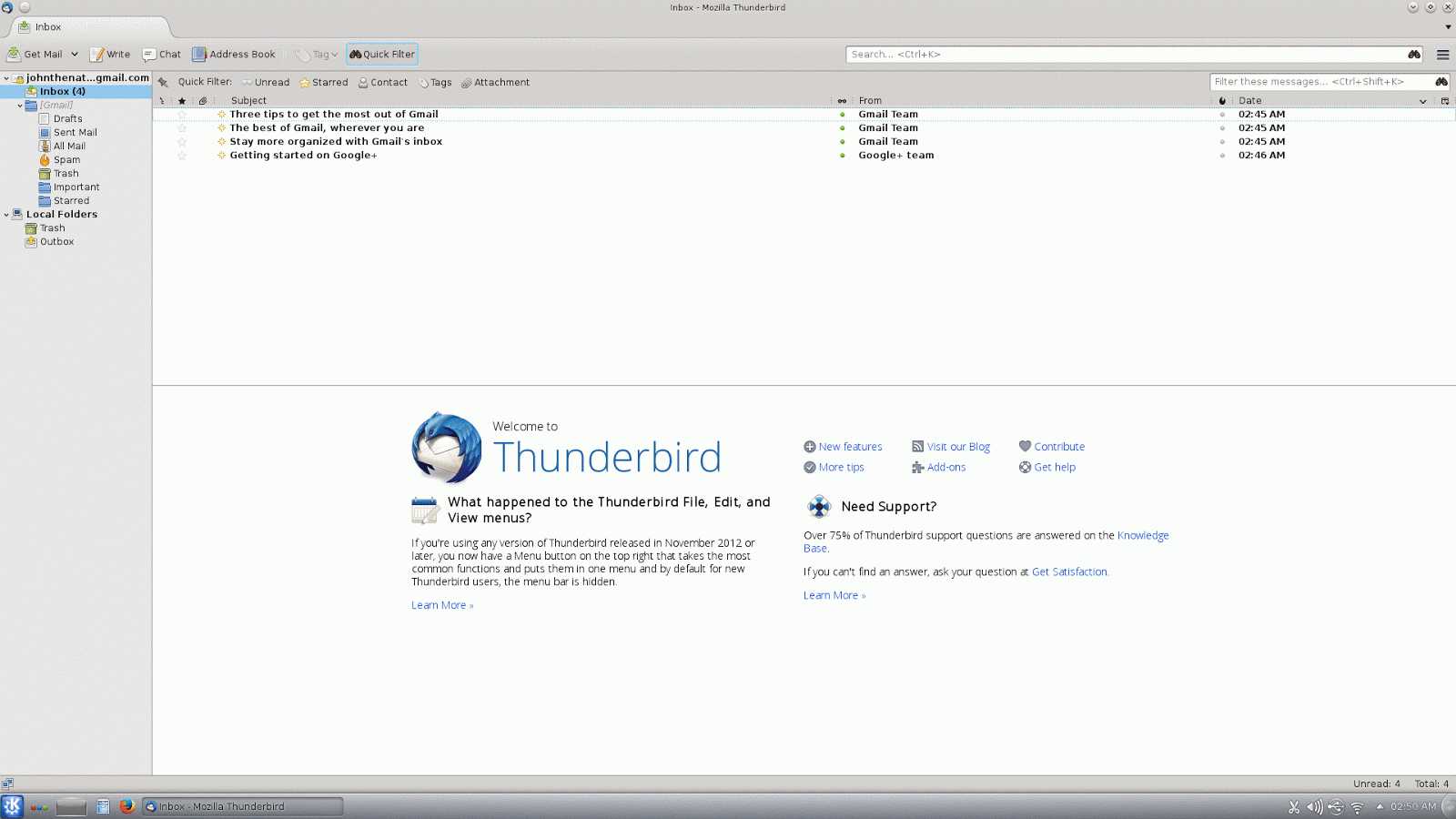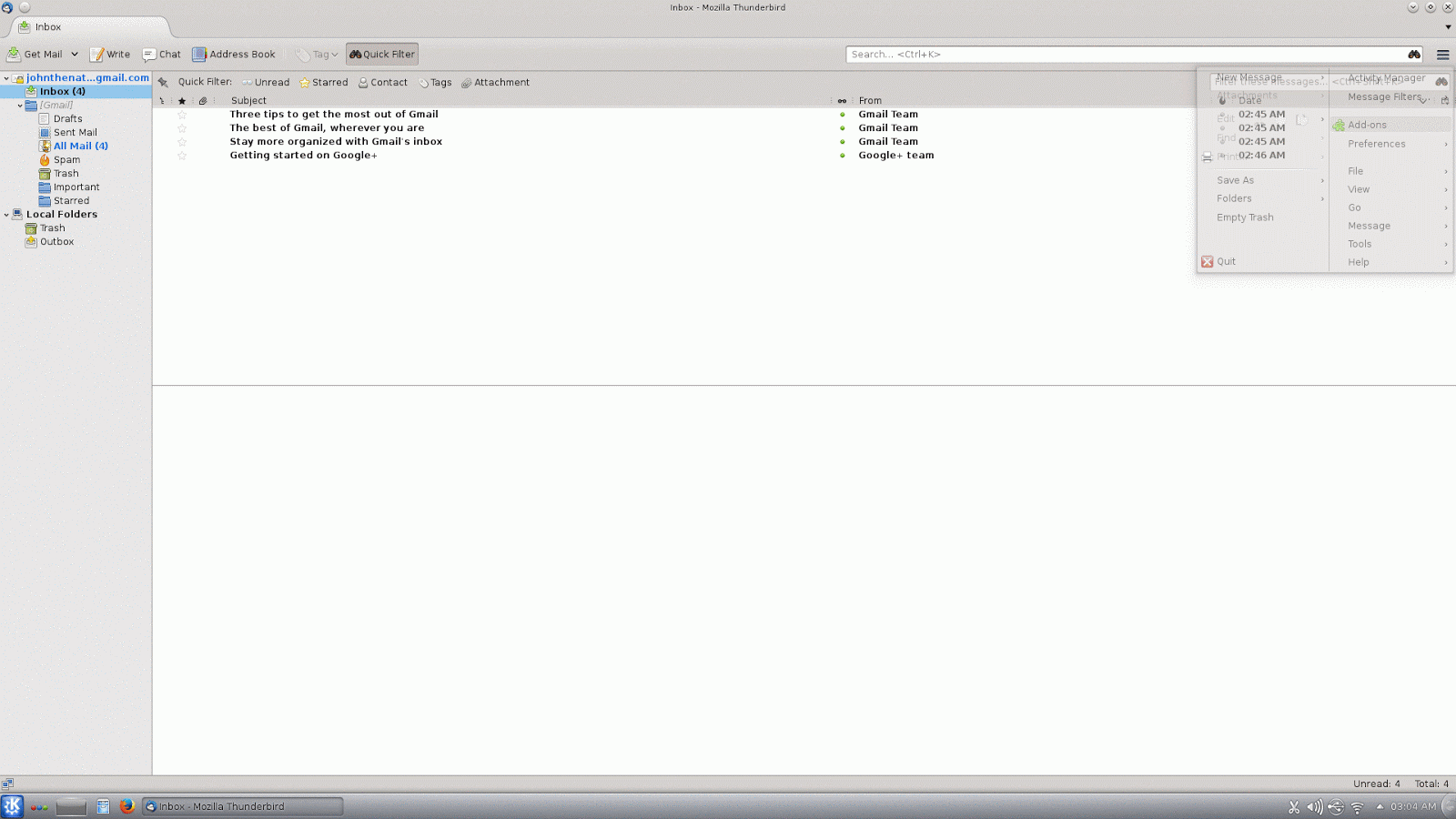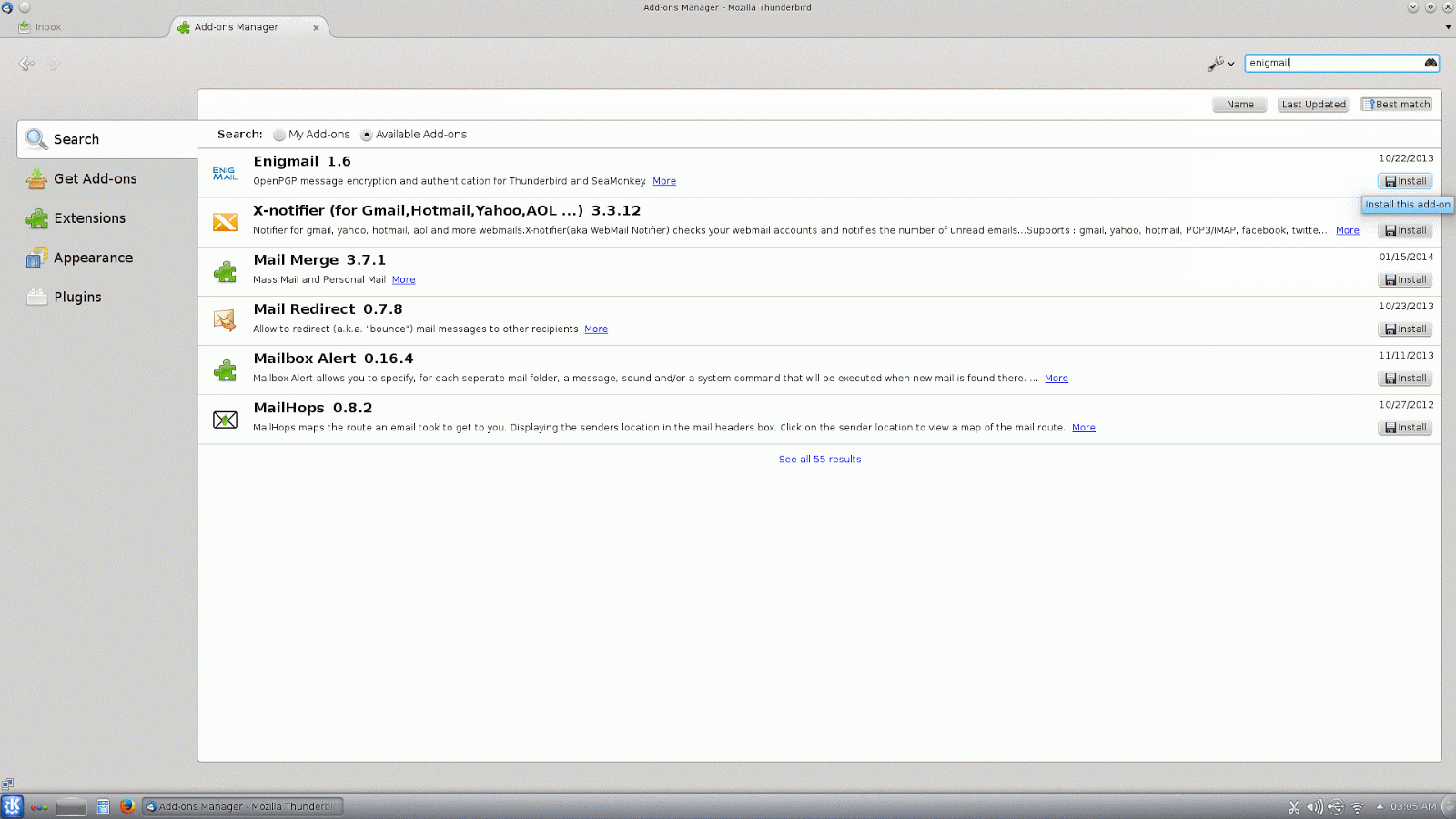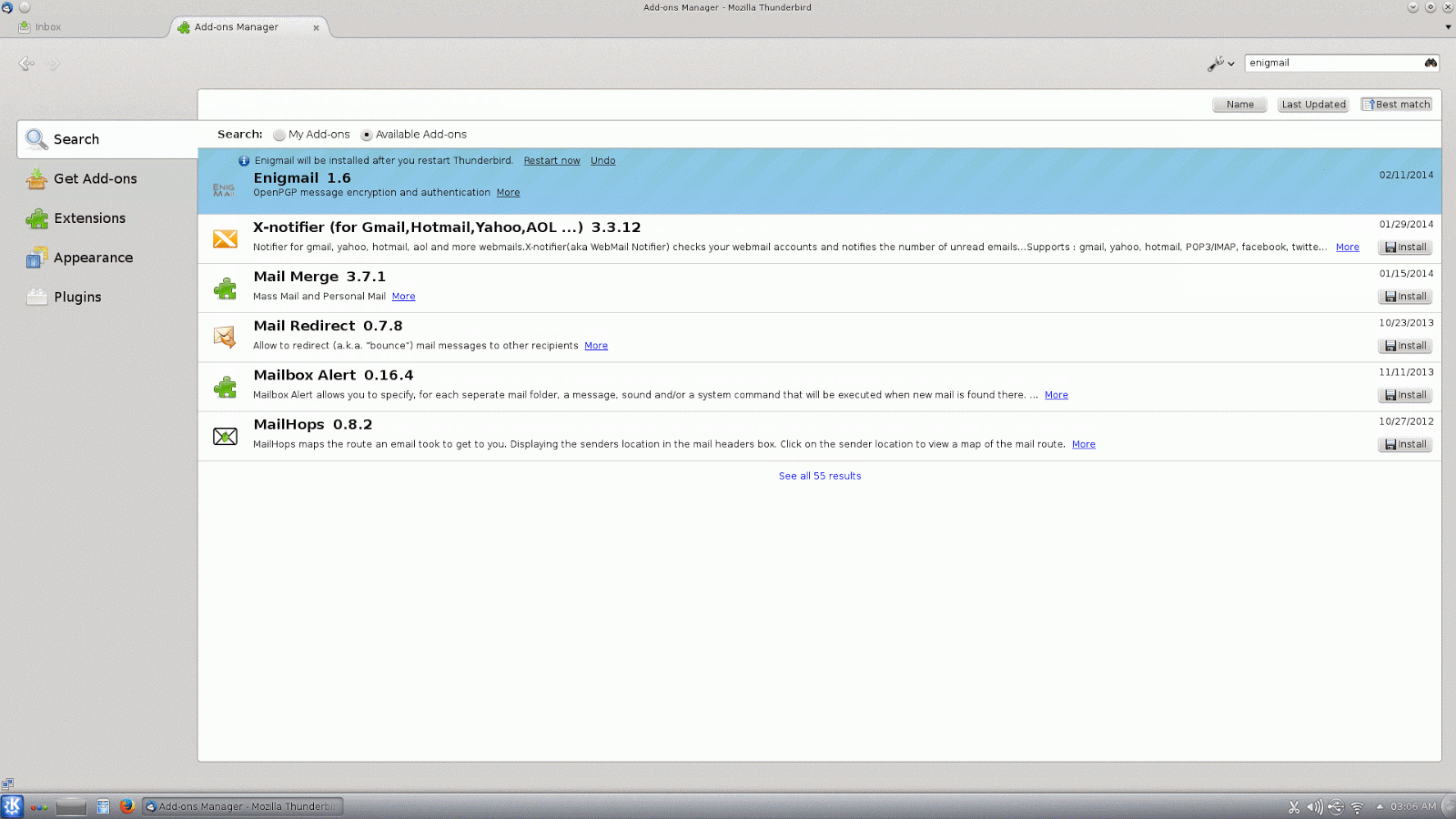
Now we need to install the Enigmail plugin in Thunderbird (if you didn't install it from your package management system on Linux as mentioned earlier). This is pretty simple and works the same whether you are running Thunderbird on Linux or Windows.In the most recent versions of Thunderbird, there is a menu button on the right which looks like three thick horizontal lines. On this menu, click on "Add-ons" and it will open a new tab for the Add-ons Manager. You can use the search box in the upper right to search for enigmail. Click on "Install" and then you will need to restart Thunderbird once it is finished.
Creating and Sharing Keys
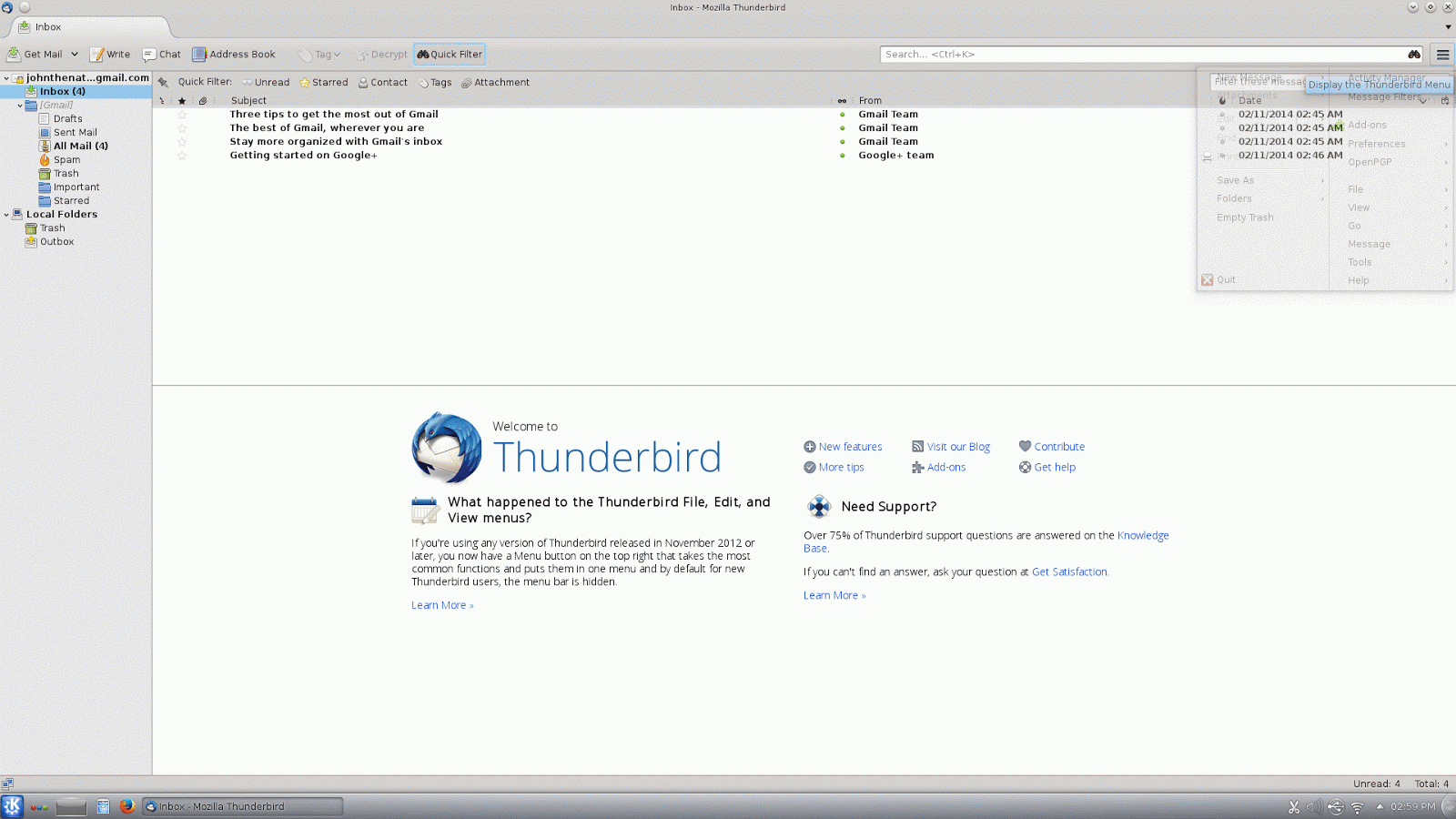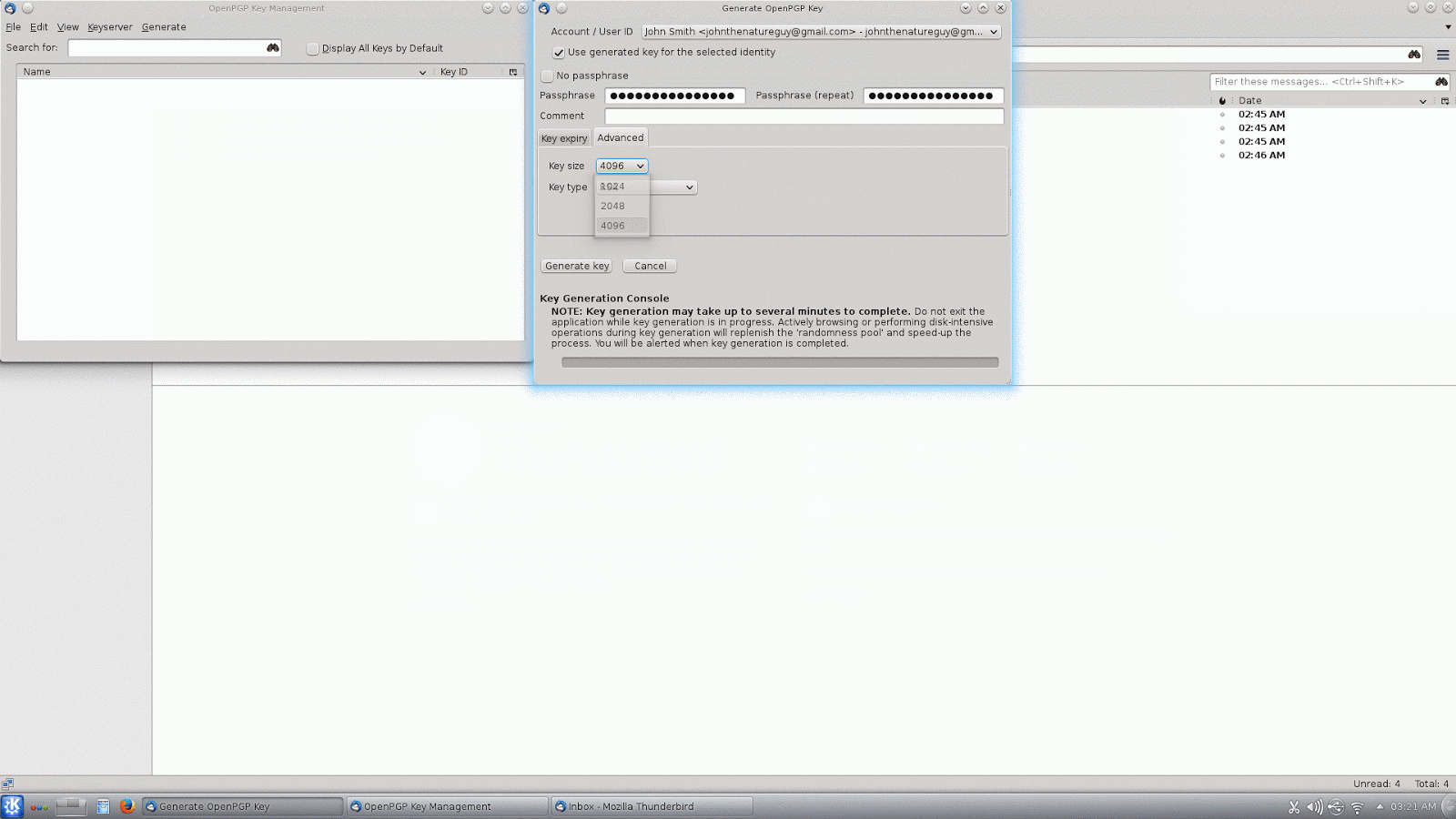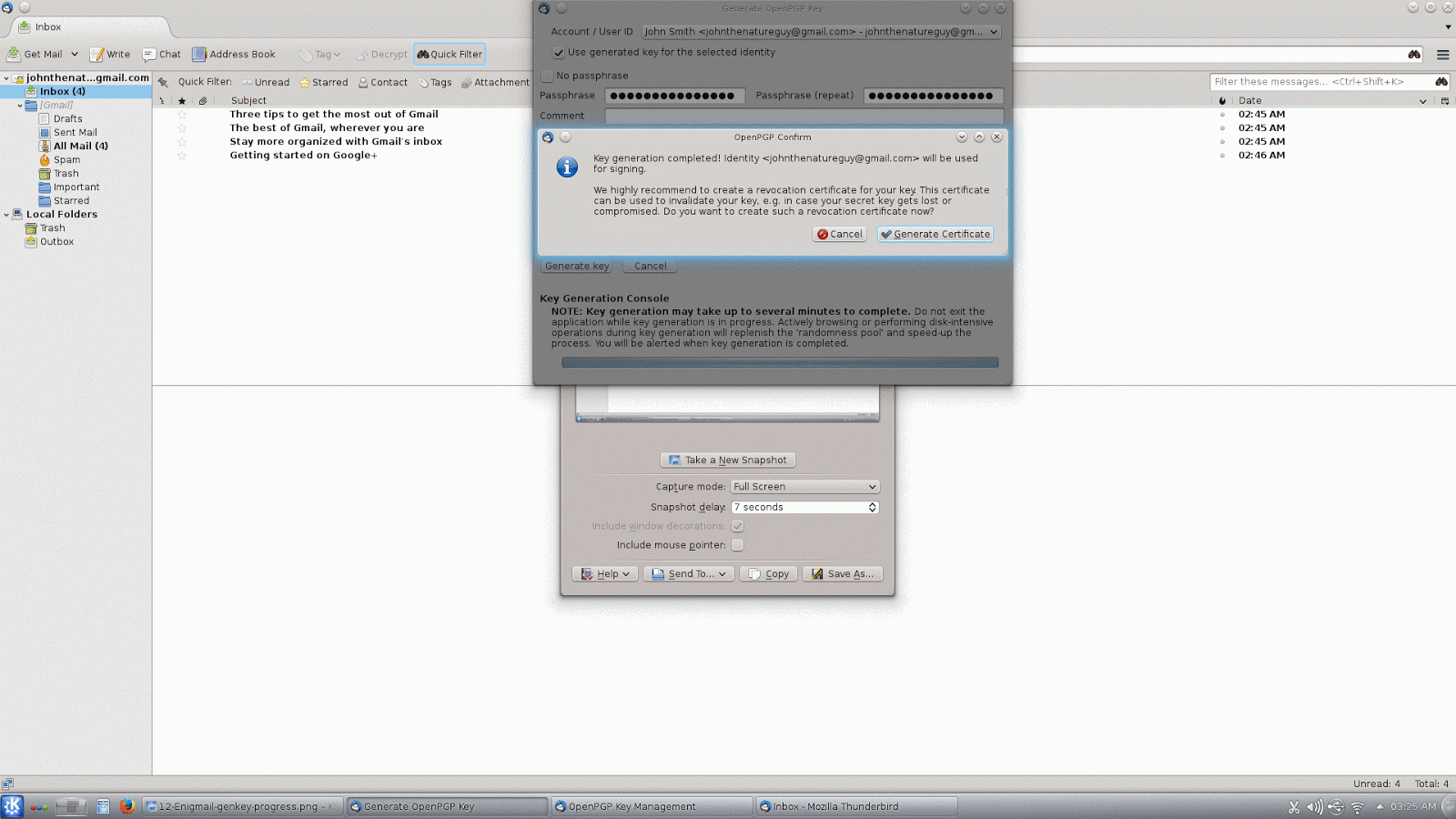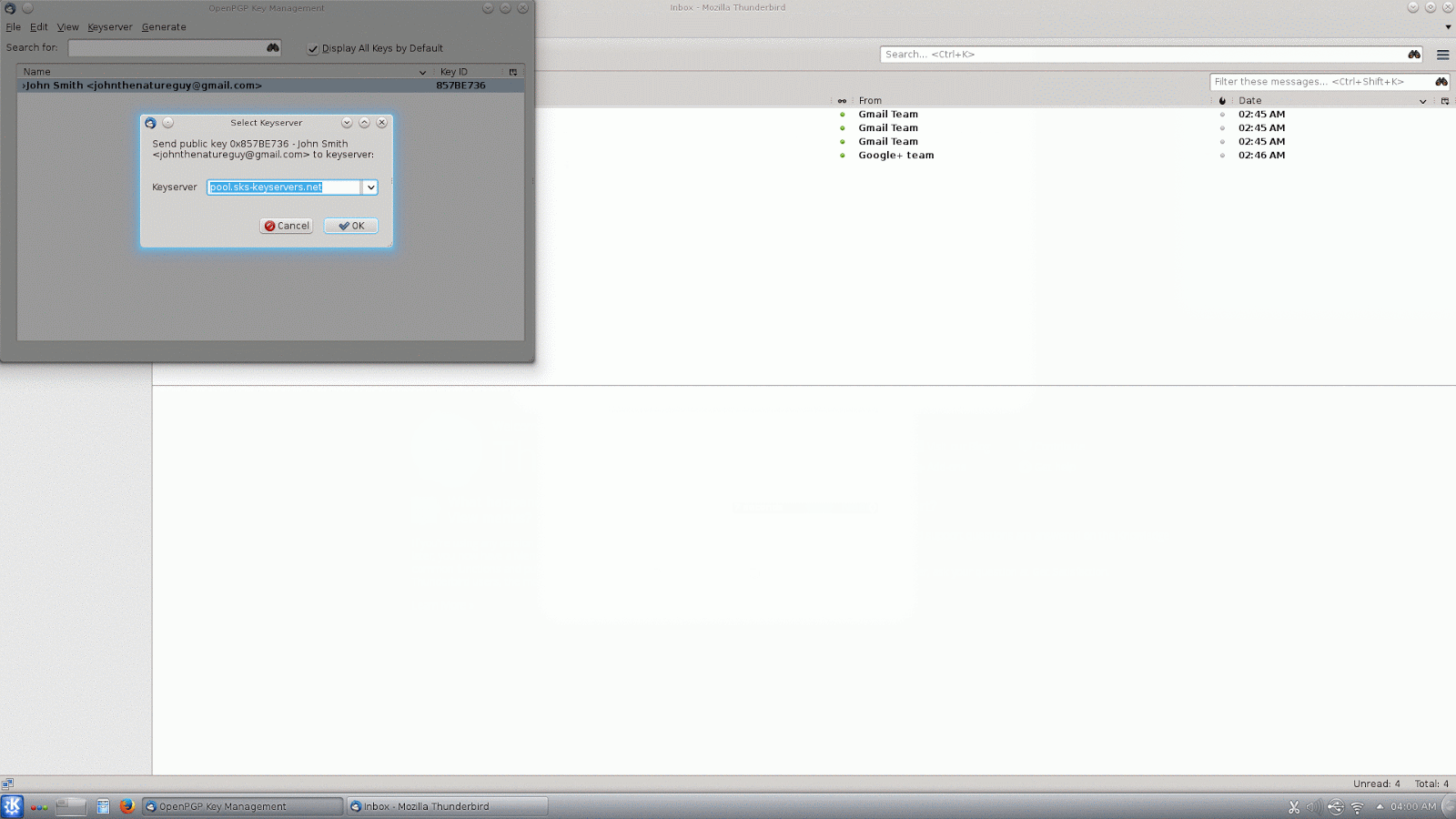
The next thing we need to do is create a key pair. Again, we will go to the menu button, this time under the "OpenPGP" menu we will click on "Key Management". This opens a new window for OpenPGP Key Management, from the menu across the top of that window click "Generate", and then "New Key Pair". You need to use a strong passphrase to protect your key pair. If you want to make your encryption stronger, under the "Advanced" tab change the key size from 2048 to 4096. (BTW, you DO want your key to expire.) Click "Generate key" and go do something else on the computer while you wait for it to finish (this can take a while). Once your key has been generated, it will offer to generate a revocation certificate. You should do this and then store it in a safe place. A revocation certificate is used to invalidate your key if it is ever compromised.Once you have generated your own key pair, you will want to upload it to a key server to share with your friends. You will need to check "Display All Keys by Default" in order to see your own key, click to select the key you just generated, then go back to the menu, click "Keyserver", and then "Upload Public Keys".
In order to use a friend's key to encrypt messages to them, you must first download their key. In order to search the key server for their key, you need to go back to the menu on the OpenPGP Key Management dialog and click "Keyserver" (the "Search for:" box is only for searching through the keys you have already downloaded, not for new ones), and then "Search for Keys". Type in the email address (Key ID if your friend has given you the ID for his current key) you want to find a key for. Once you have found and selected the keys you want, click "OK" to download them.
In order to verify that you have the right keys for each other, you will want to compare the fingerprints. You can find the fingerprint for your key, or your friend's, by right-clicking the key and then clicking "Key Properties" from the pop-up menu. The key fingerprint is near the middle of the dialog. Copy it down and compare it with what your friend got for his key to make sure they match.
Once both users have verified that they have the right key for each other, we are ready to start sending encrypted email.
Sending Encrypted Email
In order to send an encrypted email, you begin composing a message just as you normally would. Enigmail provides several places to access the settings to sign and/or encrypt your mail. There is a menu button labeled "OpenPGP" with a padlock on it and a small arrow to the right. The arrow pulls up a dropdown menu which includes options to sign and encrypt a message, clicking on the button itself pulls up a dialog box with the same options. There is also a small pair of icons at the bottom right of the message composition window, a pencil and a key. This will be highlighted, or colored, once you have selected the corresponding option to sign or encrypt the message. This gives an easy way to see the status of the message before sending. You can also click on these icons directly to encrypt or sign your message. When you send the message, it may ask for your password to access your private key (depending on your preferences and how long it has been since you last entered your password).Note that the subject line is not encrypted. So you want to make certain that you don't disclose any sensitive information in the subject line, either by keeping it vague (but potentially helping the reader classify their mail before decrypting it), or replacing it entirely with "Encrypted Message" or something.
Also, keep in mind that you can sign a message without encrypting it, or encrypt a message without signing it. Signing a message without encrypting it allows you to send a public message to a group while still allowing people to verify that the message is authentic and does come from you.
Reading Encrypted Email
When you open an encrypted email, it will appear only as a bunch of garbled nonsense until it is decrypted. Again, it may ask you for your password (depending on your settings, etc). Once we have entered the password, we can read the message.If the message was signed, we can also see that information at the top in a colored banner. Here, it states that there is an "UNTRUSTED good signature". What does that mean, and why is it untrusted? It means the message is, indeed, signed with the public key we have for the sender; but although we verified the key, we haven't done anything to indicate that we have verified it. By default, Thunderbird allows you to use a key without have given any indication that we have verified the validity of the key. So what we are seeing here is actually just fine for now (in part 2, we will learn more about this and how to mark a key as verified or trusted).
Conclusion
At this point we have learned enough to set up and use encrypted email. I've kept it to the basics to make sure this is relatively easy to get into, but I'll be writing a part 2 to introduce some more features that will make things easier for you and your friends. With these simple instructions, you can install and set up the necessary software, create and exchange keys, and send and receive secure encrypted email.So, how good is this encryption? Will it really prevent the NSA (and anyone else) from reading your email? According to Edward Snowden, "Encryption works. Properly implemented strong crypto systems are one of the few things that you can rely on. Unfortunately, endpoint security is so terrifically weak that NSA can frequently find ways around it." So what is that part about "endpoint security"? He is referring to the ends of the communication channel where the message is encrypted and decrypted, the two users' computers. If either of the systems is compromised, messages could be intercepted or forged. For instance, a virus on your computer could intercept all of your key strokes as you type them, sending the message to an attacker before it is ever encrypted. Or it could get your password when you type it, access your private key and use it to forge messages from you. It sounds rather scary, but it is worth considering that these sort of attacks are probably used primarily against priority targets, not generally as a tool of mass surveillance. So if you are simply wanting to thwart mass surveillance, and haven't done anything to actually draw the suspicions of powerful organizations like the NSA, these things may not be a major concern. Nevertheless, it would be wise to take steps to secure your system. Running an antivirus and preferably using a GNU/Linux operating system (the most popular version is Ubuntu, the one I'm using which is pictured here is Debian, from which Ubuntu is actually derived), would be a good start. But in general, yes, the techniques described here offer a high degree of protection for your digital communications.






No comments:
Post a Comment